20+ network packet diagram
BruteShark can also perform various operations like extracting DNS queries file carving extracting VoIP calls SIP RTP Building network diagram for users and network nodes extracting authentication hashes using Hashcat NTLM HTTP-Digest CRAM-MD5 Kerberos etc and retrieving and encoding passwords and usernames. Packet Tracer 80 - Setting up and managing a DHCP server Details Last Updated.
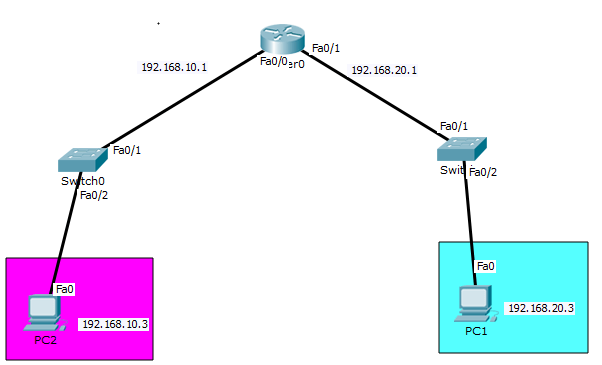
How Does A Packet Flow Network Kings
Learn how to use Deep packet analysis to discovery and monitor the way people access your servers and interfaces on a granular level.

. Level 2 shows the data links. By default the Cisco ASA 5505 firewall denies the traffic entering the outside interface if no explicit ACL has been defined to allow the traffic. Regional external HTTPS load balancer.
An intrusion detection system IDS. On the ARPANET the starting point for host-to-host communication in 1969 was the 1822 protocol which defined the. OSI subdivides the Network Layer into three sublayers.
The lithium-ion battery an indispensable energy source for modern mobile phones was commercialized by Sony and Asahi Kasei in 1991. A bridge in a computer network is one kind of network device used to separate a network into sections. Every section in the network represents a collision domain that has separate bandwidth.
Test your ability to configure port security on a cisco 2960 switch in Packet Tracer 721 to prepare cisco ICND1 certification exam. These are most commonly used to map human-friendly domain names to the numerical IP. It can be used to.
300 in free credits and 20 free products. To ensure that all Wikipedia content is verifiable Wikipedia provides a means for anyone to question an uncited claimIf your work has been tagged please provide a reliable source for the statement and discuss if needed. It is now maintained by the.
Priced at a rate per host of 5 per month when paid annually or 720 month to month. Also intrusion prevention system or IPS is a device or software application that monitors a network or systems for malicious activity or policy violations. The resource records contained in the DNS associate domain names with other forms of information.
A virtual private network VPN extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Also known as the network layer L3 is an abstraction layer that deals with packet forwarding through intermediate routers. Here is our list of the top network diagram drawing topology and mapping tools.
The Ultimate Network Diagram Guide - Understand the history of network diagrams and learn about common symbols. It is one of the core protocols of standards-based internetworking methods in the Internet and other packet-switched networks. IPv4 was the first version deployed for production on SATNET in 1982 and on the ARPANET in January 1983.
GPRS was established by European Telecommunications Standards Institute ETSI in response to the earlier CDPD and i-mode packet-switched cellular technologies. General Packet Radio Service GPRS is a packet oriented mobile data standard on the 2G and 3G cellular communication networks global system for mobile communications GSM. The Domain Name System DNS is the hierarchical and decentralized naming system used to identify computers reachable through the Internet or other Internet Protocol IP networks.
Internet Protocol version 4 IPv4 is the fourth version of the Internet Protocol IP. To create and maintain routing information OSPF routers complete the following generic link-state routing process shown in Figure 3-1 to reach a state of convergence. See examples and learn how to make a network diagram from scratch.
DHCP service is a key component of your network infrastructure by allowing centralized ip address management on a single pool of. If the Client does not receive a CONNACK Packet from the Server within a reasonable amount of time the Client SHOULD close the. Trang web về thủ thuật điện thoại máy tính mạng học lập trình sửa lỗi máy tính cách dùng các phần mềm phần mềm chuyên dụng công nghệ khoa học và cuộc sống.
It is a network of networks that consists of private public academic business and government networks of local to global scope linked by a broad array of electronic wireless and optical networking. Googles production network handles packet routing. ASCII characters only characters found on a standard US keyboard.
It is still used to route most Internet traffic today even with the. The CONNACK Packet is the packet sent by the Server in response to a CONNECT Packet received from a Client. You can add a citation by selecting from the drop-down menu at the top of the editing boxIn markup you can add a citation manually using ref tags.
OSPF Operation Overview. The benefits of a VPN include increases in functionality security and management of the private networkIt provides access to resources. OSPF-enabled routers must form adjacencies with their neighbor before they can share information with that neighbor.
Must contain at least 4 different symbols. The first packet sent from the Server to the Client MUST be a CONNACK Packet MQTT-320-1. Interface FastEthernet02 switchport mode access switchport voice vlan 20 switchport port-security switchport port-security maximum 3 switchport port-security mac-address sticky.
ACM Transactions on Recommender Systems TORS will publish high quality papers that address various aspects of recommender systems research from algorithms to the user experience to questions of the impact and value of such systemsThe journal takes a holistic view on the field and calls for contributions from different subfields of computer science and. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management SIEM system. So that network performance can be improved using a bridge.
The Internet or internet is the global system of interconnected computer networks that uses the Internet protocol suite TCPIP to communicate between networks and devices. This diagram shows the components of a global external HTTPS load balancer deployment. One of the first uses of the term protocol in a data-commutation context occurs in a memorandum entitled A Protocol for Use in the NPL Data Communications Network written by Roger Scantlebury and Keith Bartlett in April 1967.
This lab will show you how to configure site-to-site IPSEC VPN using the Packet Tracer 721 ASA 5505 firewall. In telecommunications packet switching is a method of grouping data into packets that are transmitted over a digital networkPackets are made of a header and a payloadData in the header is used by networking hardware to direct the packet to its destination where the payload is extracted and used by an operating system application software or higher layer protocols. In 2001 the third generation was launched in Japan by NTT DoCoMo on the WCDMA standardThis was followed by 35G 3G or turbo 3G enhancements based on the high-speed packet access HSPA family allowing UMTS.
Wednesday 01 September 2010 2030 Written by PacketTracerNetwork. 3a Subnetwork Access 3b Subnetwork Dependent Convergence and 3c Subnetwork Independent Convergence. 6 to 30 characters long.
Thursday 08 April 2021 0610 Published. In the OSI model a bridge works at layer-2 namely the data link layer. It was designed to provide a unified data-carrying service for both circuit-based clients and packet-switching clients which provide a datagram-based service model.

Network Packet Structure During The Websocket Session Download Scientific Diagram

Sample Ip Packet Structure Download Scientific Diagram
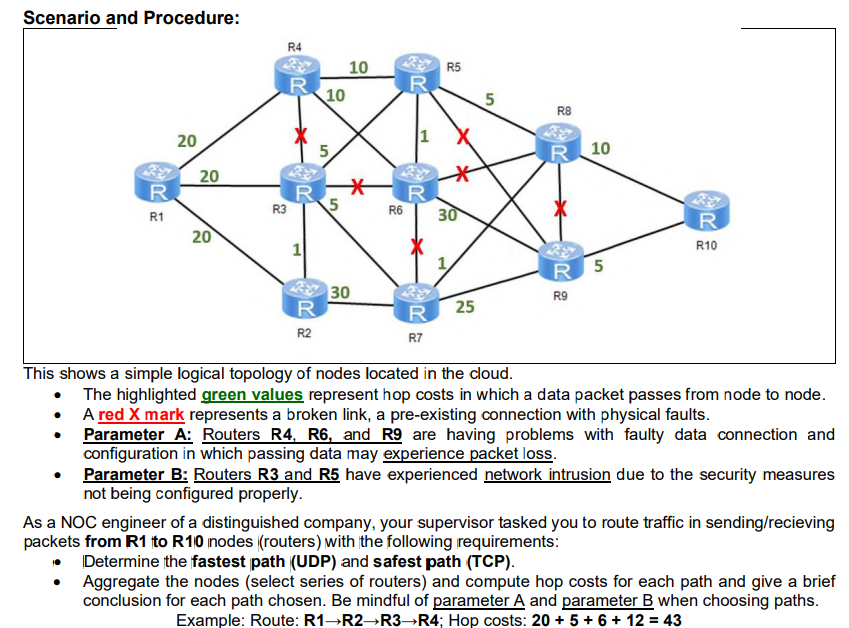
Solved Scenario And Procedure 20 R D R1 20 R3 R4 R R 1 10 Chegg Com

Flow Diagram Of Packet In Process Download Scientific Diagram

Simple Local Area Network Lan Berbagisolusi Ethernet Cable Computer Maintenance Local Area Network

Ethernet Packet Format With Sid List Download Scientific Diagram

Data Link Sub Layers As Listed In 20 Download Scientific Diagram

Packet Structure An Additional Two Status Bytes 20 And 21 Are Used Download Scientific Diagram

6 Bluetooth Link Controller State Diagram 20 Download Scientific Diagram

Diagram Of The Udp Packet Format A 20 Byte Header Was Used To Locate Download Scientific Diagram

Ppdu Format 10 Figure 20 1 Download Scientific Diagram

Ethernet Network Model For 20 Ethernet Nodes Scenario 1 Download Scientific Diagram
Network Diagram For Expansion From One Ap To 3 Ap A First Of All We Download Scientific Diagram

Encoding And Decoding In A Three Layered Auto Encoder Network Second Download Scientific Diagram

Spine Leaf 4 4 20 Evaluation Topology Download Scientific Diagram

Ethernet Packet Processor An Outline Of The Proposed Architecture Download Scientific Diagram

Linear Topology A 10 Nodes B 20 Nodes C 30 Nodes D 40 Nodes Download Scientific Diagram